Getting Started with Terraform Preconditions
December 4, 2024Snap to Roads is now available for Azure Maps
December 4, 2024This one is going to be quick. The question is the following: if you have an Network Security Group rule in Azure that matches any protocol, but a specific TCP or UDP port number, what is the effect? Would protocols such as ICMP be matched as well?
To verify this I have this NSG:
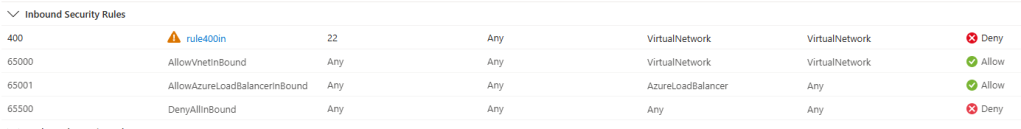
If you look at the first rule, it is dropping traffic on port 22 matching any protocol. I deployed two virtual machines in a subnet where this NSG is applied:
$ az vm list-ip-addresses -g $rg -o table
VirtualMachine PrivateIPAddresses
---------------- --------------------
vm1 10.13.76.4
vm2 10.13.76.5As expected, virtual machines cannot SSH into each other, because the NSG is dropping that traffic (matching on the “port 22” and the “any protocol” portions of the rule):
jose@vm1:~$ ssh 10.13.76.5
ssh: connect to host 10.13.76.5 port 22: Connection timed outBut will ICMP traffic be dropped too? It is matching on the “any protocol” part of the NSG rule, but it is not matching on the “port 22” bit. Since all parts of a single rule are joined with a logical “and”, the overall result is that the rule will not match ICMP traffic, and it will consequently not drop it. As you can see here, virtual machines can happily ping each other:
jose@vm1:~$ ping 10.13.76.5
PING 10.13.76.5 (10.13.76.5) 56(84) bytes of data.
64 bytes from 10.13.76.5: icmp_seq=1 ttl=64 time=1.71 ms
64 bytes from 10.13.76.5: icmp_seq=2 ttl=64 time=1.16 ms
64 bytes from 10.13.76.5: icmp_seq=3 ttl=64 time=2.32 ms
^CThe corollary of this post is that if you are writing rules that should match on any protocol, you should make sure that you don’t specify any port number. Otherwise the rule will not work correctly.