AI Toolkit for VS Code February Update
February 20, 2025Kevään Microsoft AI Tour 18.3.2025
February 21, 2025The Network Security Group (NSG) is the primary mechanism for segmenting a subnet in Microsoft Azure. NSGs are commonly implemented. Unfortunately, people assume quite a bit about NSGs, and I want to tackle that by explaining why you need to be aware of the default rules in Network Security Groups.
The Assumption
Let’s say I have an extremely simple workload consisting of:
- A virtual machine acting as a web server.
- A virtual machine acting as a database server.
Yes, this could be VNet-connected PaaS services and have the same issues, but I want the example to be as clear as possible.
I want to lock down and protect that subnet so I will create an NSG and associate it with the subnet. Traffic from the outside world is blocked, right? Now, I will create an inbound rule to allow HTTPS/TCP 443 from client external addresses to the web server.
| Name | Source | Protocol | Port | Destination | Action |
| AllowWeb | TCP | 443 | Web VM | Allow |
The logic I expect is:
- Allow web traffic from the clients to the web server.
- Allow SQL traffic from the web server to the database server in the same subnet.
- Everything else is blocked.
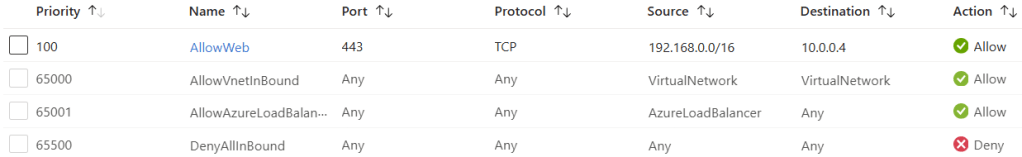
I check the Inbound Rules in the NSG and I can see my custom rules and the built-in default rules. This confirms my logic, right?
All is well, until one day, every computer in the office has a ransomware demand screen and both of my Azure VMs are offline. Now my boss is screaming at me because the business’s online application is not selling our products to customers.
Where It All Went Wrong
Take a look at the default rules in the above screenshot. Rule 65500 denies all traffic. That’s what we want; block all traffic where a higher priority rule doesn’t allow it. That’s the rule that we were banking on to protect our Azure workload.
But take a look at rule 65000. That rule allows all traffic from VirtualNetwork to VirtualNetwork. We have assumed that VirtualNetwork means the virtual network that the NSG of the subnet that it is associated with – in other words, the virtual network that we are working on.
You are in for a bigger surprise than a teddy bear picnic in your woods if you research the definition of VirtualNetwork:
The virtual network address space (all IP address ranges defined for the virtual network), all connected on-premises address spaces, peered virtual networks, virtual networks connected to a virtual network gateway, the virtual IP address of the host, and address prefixes used on user-defined routes. This tag might also contain default routes.
In summary, this means that VirtualNetwork contains:
- The prefixes in your virtual network
- Any peered virtual networks
- Any remote networks connected by site-to-site networking
- Any networks where you have referenced in a user-defined route in your subnets.
Or, pretty much every network you can route to/from. And that’s how the ransomware got from someone’s on-premises PC into the virtual network. The on-premises networks were connected with the Azure virtual network by VPN. The built-in 65000 rule allowed all traffic from on-premises. There was nothing to block the ransomware from spreading to the Azure VMs from the on-premises network.
Solving This Problem
There are a few ways to solve this issue. I’ll show you a couple. I am a believer in true micro-segmentation to create trust-noone networks. The goal here is that no traffic is allowed anywhere on any Azure network without a specific rule to permit flows that are required by the business/technology.
The logic of the below is that all traffic will be denied by default, including traffic inside the subnet.
Remember, all NSG rules are processed at the NIC, no matter how the NSG is associated.

I have added a low-priority (4000) rule to deny everything that is not allowed in the higher-priority rules. That will affect all traffic from any source, including sources in the same virtual network or subnet.
By the way, the above is the sort of protection that many national cyber security agencies are telling people to implement to stop modern threats – not just the threats of 2003.
I know that some of you will prefer to treat the NSG as an edge defence, allowing all traffic inside the virtual network. You can do that too. Here’s an example of that:

My rule at 3900 allows all traffic inside the address prefix of the virtual network. The following rule, 4000, denies everything, which means that anything from outside the network (not including the traffic in rule 100) will be blocked.
The Lesson
Don’t assume anything. You now know that VirtualNetwork means everything that can route to your virtual network. For example the Internet service tag includes The Internet and Microsoft Azure!
The post Beware Of The Default Rules In Network Security Groups first appeared on Aidan Finn, IT Pro.