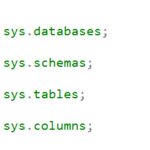
T-SQL 101: #127 Querying the SQL Server System Catalog
March 10, 2025Hanging Up My MVP Award
March 10, 2025
Kinde supports SAML but only as a SP.
The Kinde SAML documentation is here.
The B2C SAML IDP configuration is described here.
The B2C custom policy needed for the metadata is described here.
Kinde
The SAML functionality needs to be added as a Kinde custom SAML enterprise connection.
Configure the connection as follows.
Everything else was just left to the default setting.
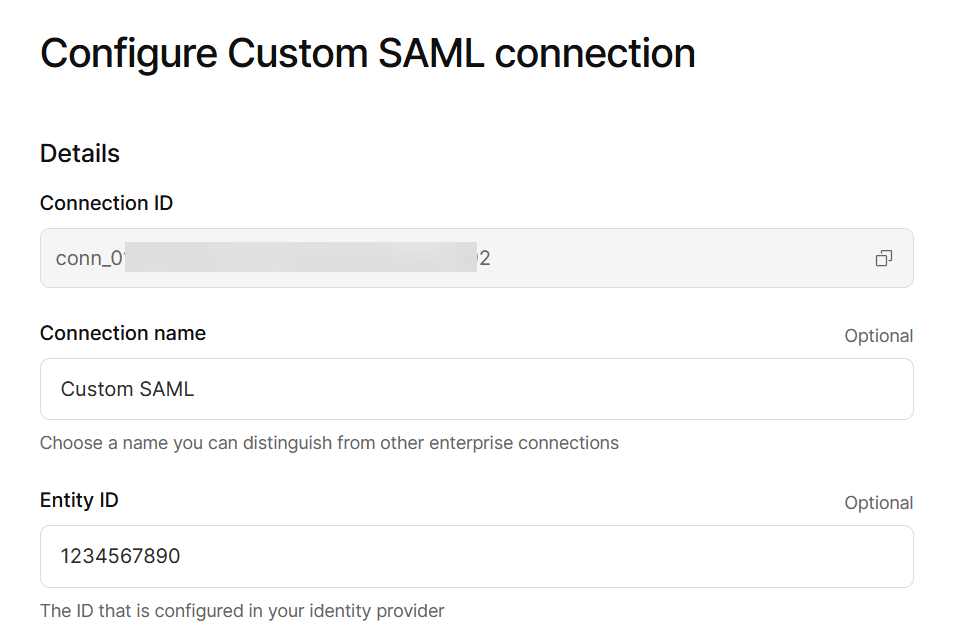
You can use any value for the entity ID.
The B2C metadata URL is:
https://tenant.b2clogin.com/tenant.onmicrosoft.com/
/Samlp/metadata

The enterprise connection is connected to my Kinde .NET sample.
I used the Kinde .NET sample to test this.
Set the client ID and secret in the sample to those of your Kinde application.
B2C
Create a B2C test user and ensure that the user has a display name, first name, last name and email address.
Set up a B2C app. registration as described here.
In the manifest of the app. registration, make the following changes:
"identifierUris": [
"1234567890"
],
where the “identifierUris” matches the Kinde entity ID above.
"api": {
"acceptMappedClaims": null,
"knownClientApplications": [],
"requestedAccessTokenVersion": 2,
"oauth2PermissionScopes": [],
"preAuthorizedApplications": []
},
Set “requestedAccessTokenVersion” to 2.
"web": {
"homePageUrl": null,
"logoutUrl": null,
"redirectUris": [
"https://azureid.kinde.com/login/saml/callback"
],
"implicitGrantSettings": {
"enableAccessTokenIssuance": false,
"enableIdTokenIssuance": false
},
"redirectUriSettings": [
{
"uri": "https://azureid.kinde.com/login/saml/callback",
"index": null
}
]
},
Set the “redirectUris” where the redirect settings map to the Kinde ACS above.
Run the Kinde .NET app
When I run it:
Sign in.
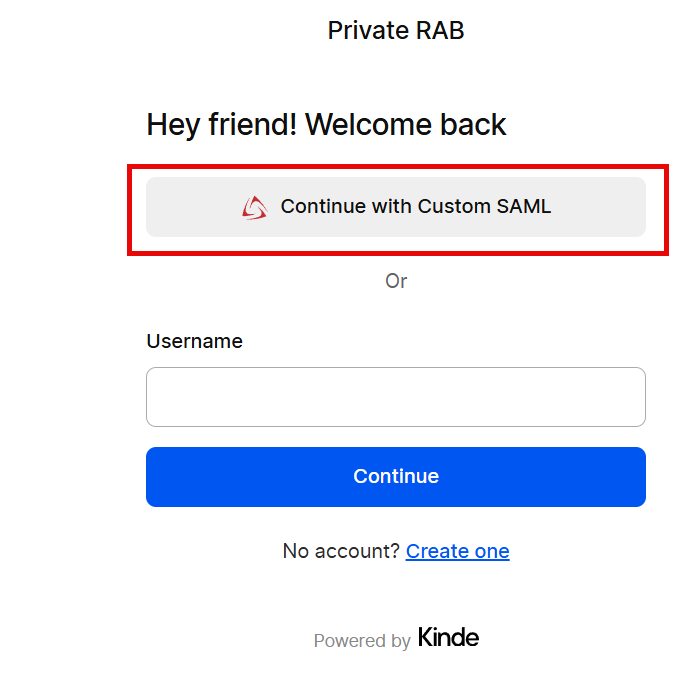
Choose the custom SAML option.
This brings up the B2C login page:
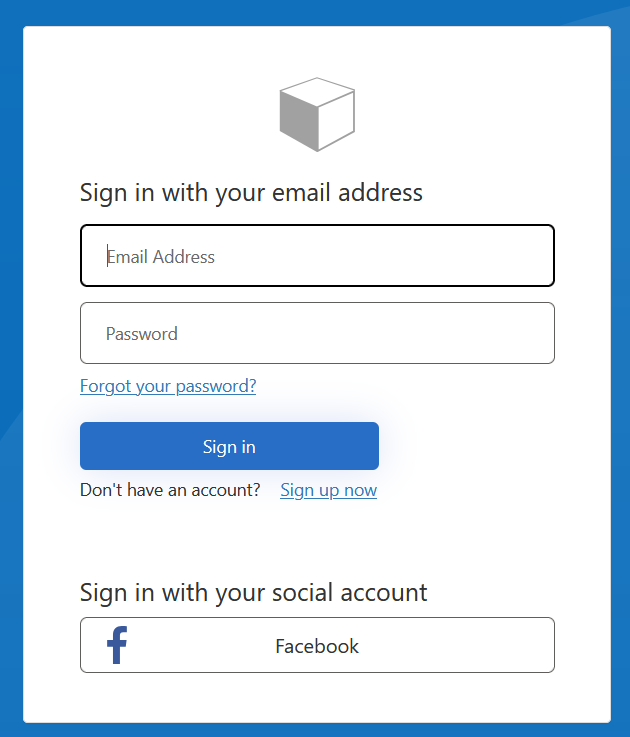
Sign in with your B2C credentials.
If this is the first time you are using that user account, you get:
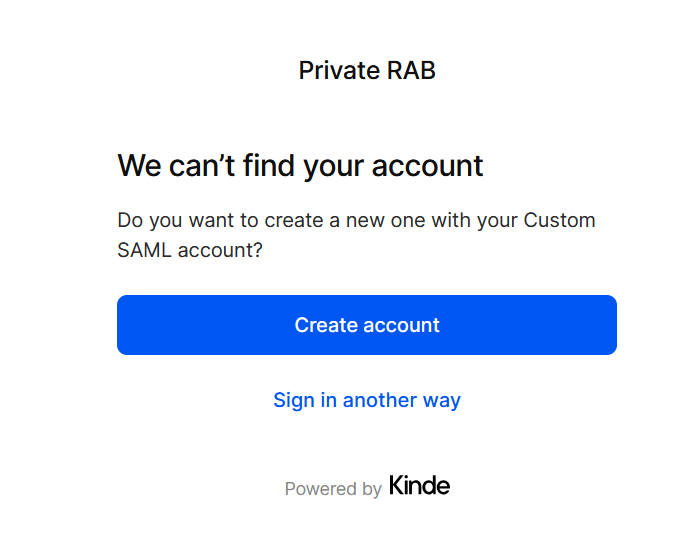
Click “Create account”.
Note: You can avoid this by turning on the setting:
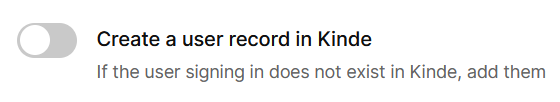
You then get:
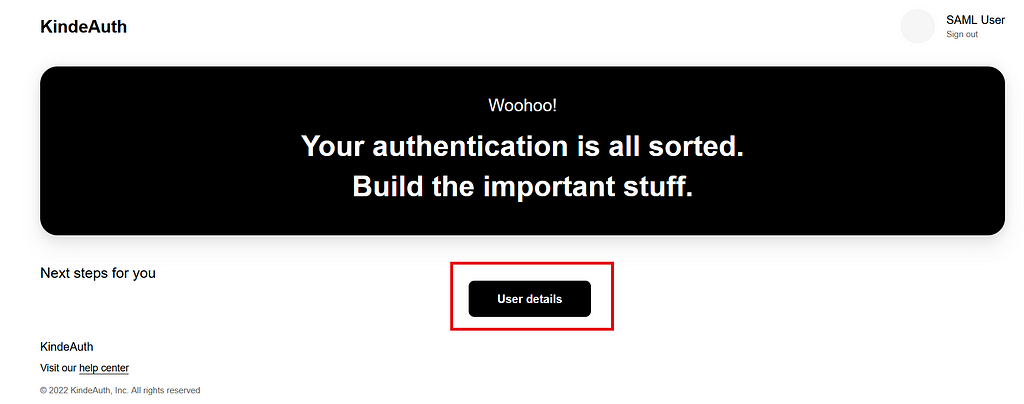
Click “User details”.
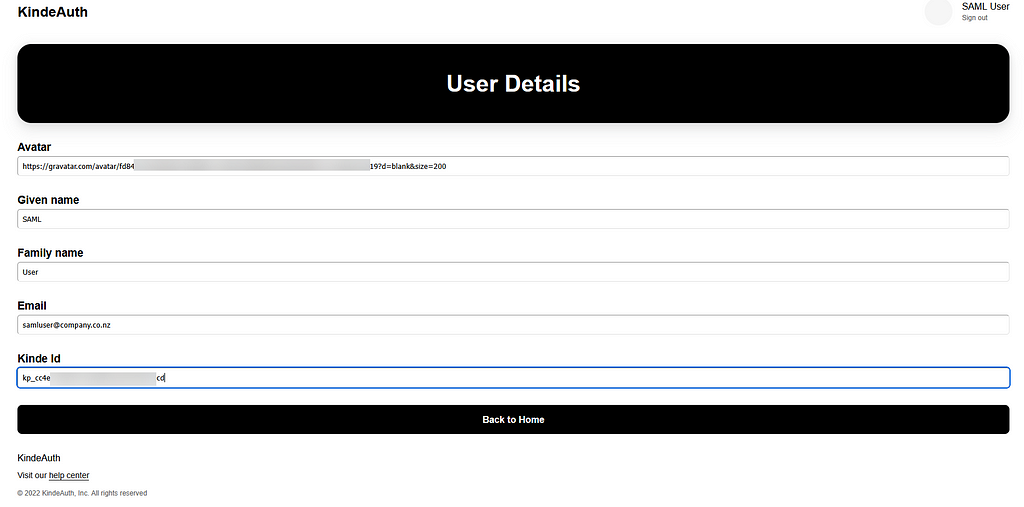
If you look at a network trace, you will see the following in the SAML authorization response.
<saml:Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims
/name" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"
FriendlyName="Display Name">
SAML User
<saml:Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims
/givenname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" FriendlyName="Given Name">
SAML
<saml:Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims
/surname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"
FriendlyName="Surname">
User
<saml:Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims
/emailaddress" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:
uri" FriendlyName="Email Address">
samluser@company.co.nz</saml:
AttributeValue>
<saml:Attribute Name="http://schemas.microsoft.com/identity/claims/
userprincipalname" NameFormat="urn:oasis:names:tc:SAML:2.0:
attrname-format:uri" FriendlyName="UserPrincipalName">
841...543@tenant.onmicrosoft.com
All good!
Connecting Kinde as an SP to Azure AD B2C via SAML was originally published in The new control plane on Medium, where people are continuing the conversation by highlighting and responding to this story.