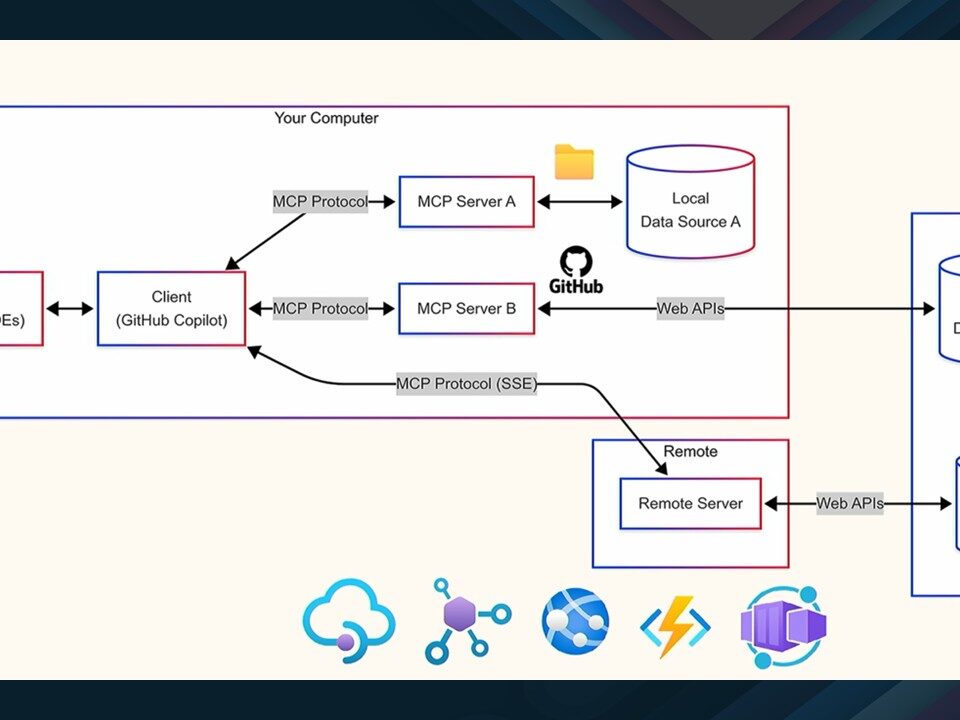
Using GitHub Models with Semantic Kernel
April 16, 2025Introducing the Microsoft Graph Copilot PowerShell module
April 16, 2025
I found this post to be helpful.
To get Graph Explorer to work for these tenants, you need to:
- Create or use an internal user in your organisation to log in, e.g. user@tenant.onmicrosoft.com
- Run in an incognito window
- Use this URL
https://developer.microsoft.com/en-us/graph/graph-explorer?tenant=tenant.onmicrosoft.com
- Or
https://developer.microsoft.com/en-us/graph/graph-explorer?tenant=tenant ID
If you don’t, you will probably SSO to the main Entra ID tenant instead of the CIAM one.
You don’t need to create an application registration, secret key, etc.
To create an internal user:

Authenticate with your internal user and then check by running:

GET v1.0 https://graph.microsoft.com/v1.0/me
Note: The same principles and commands apply to both Azure AD B2C and Entra External ID.
However, when you try to log in to Entra External ID, you get the error:
“The domain is not a valid login domain for the account type”.
The only way around this is to make that user a Global Admin 😢
Extension attributes
To get a list of extension attributes, such as extension_abc, used in custom policies, you need to get the client ID and object ID of the B2C extension app.
https://graph.microsoft.com/v1.0/applications/object ID/extensionProperties
You will get:
"code": "Authorization_RequestDenied",
"message": "Insufficient privileges to complete the operation.",

You need to “Modify Permissions” and then “Consent”.
You may get:

In this case, use the admin account link and sign in as an admin.

Accept as an admin.

Then consent to the application.
The permission is now granted.

Then keep running and consenting until you see the result:
{
"value": [
{
"id": "5aa...51d",
"deletedDateTime": null,
"appDisplayName": "",
"dataType": "String",
"isMultiValued": false,
"isSyncedFromOnPremises": false,
"name": "extension_51f...e4e_mfaPhoneNumber",
"targetObjects": [
"User"
]
},
]
}
To see which extension attributes a user has, use:
https://graph.microsoft.com/v1.0/users/user id
?$select=displayName,extension_extension app client ID_privacyPolicy
To add an extension attribute to a user, use:
PATCH https://graph.microsoft.com/v1.0/users/user ID
with Request Header set to:

"Content-Type" set to "application/json"

Request Body set to:
{
"extension_51f...e4e_mfaPhoneNumber": "02112345678"
}
You will have to consent to “User.ReadWrite.All”.
And you get back:
No Content - 204
To check, run:
https://graph.microsoft.com/v1.0/users/user object ID?
$select=displayName,extension_51f...e4e_mfaPhoneNumber
And you get back:
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#users
(displayName,extension_51f...e4e_mfaPhoneNumber)/$entity",
"displayName": "Tom James",
"extension_51f...e4e_mfaPhoneNumber": "02112345678"
}
Users
You can get a basic set of attributes with “…/v1.0/me” but to get more user details, you have to use select clauses, e.g.:
GET v1.0 https://graph.microsoft.com/v1.0/users/
user object ID?$select=displayName,givenName,surname,
mail,jobTitle,department
Remove the CR before running. I added them for readability.
You will get:
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#users/$entity",
"@microsoft.graph.tips": "This request only returns a subset of the resource'
s properties. Your app will need to use $select to return non-default
properties. To find out what other properties are available for this resource
see https://learn.microsoft.com/graph/api/resources/user",
"businessPhones": [],
"displayName": "Joe Bloggs",
"givenName": null,
"jobTitle": null,
"mail": null,
"mobilePhone": null,
"officeLocation": null,
"preferredLanguage": null,
"surname": null,
"userPrincipalName": "joeb@tenant.onmicrosoft.com",
"id": "4de...d78"
}
To get back all the user attributes, run:
GET https://graph.microsoft.com/beta/users/user object ID
Note the “beta”.
And you get back a lot of attributes:
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#users/
$entity", "@microsoft.graph.tips": "Use $select to choose ...",
"id": "d8e...6f9",
"deletedDateTime": null,
"accountEnabled": true,
"ageGroup": null,
"businessPhones": [],
"city": null,
"createdDateTime": "2021-10-25T03:10:45Z",
"creationType": "LocalAccount"
...
}
To create a user, use:

POST https://graph.microsoft.com/v1.0/users
with Request Header:
"Content-Type" set to "application/json"
and Request Body:
{
"accountEnabled": true,
"displayName": "Adele Soprano",
"mailNickname": "AdeleS",
"userPrincipalName": "AdeleS@tenant.onmicrosoft.com",
"passwordProfile" : {
"forceChangePasswordNextSignIn": true,
"password": "somepassword"
}
}
You will get:
Created - 201
and:
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#users/$entity",
"id": "742...7ba",
"businessPhones": [],
"displayName": "Adele Soprano",
"givenName": null,
"jobTitle": null,
"mail": null,
"mobilePhone": null,
"officeLocation": null,
"preferredLanguage": null,
"surname": null,
"userPrincipalName": "AdeleS@tenant.onmicrosoft.com"
}
All good!
Using the Graph Explorer for user CRUD in Azure AD B2C and Entra External ID was originally published in The new control plane on Medium, where people are continuing the conversation by highlighting and responding to this story.