Building an Automated Recovery Pipeline for GPU Clusters with Slurm on Azure Part 2
June 13, 2025Announcing a new workshop experience for AI Gateway for Azure API Management.
June 13, 2025
Note that this code is not production-ready, so use it at your own risk!
Note: You can also provision the phone number manually in the “Authentication Methods” section.

Note that these two user attributes are for contacting someone, not for MFA.

This is about the older “PhoneFactor-InputOrVerify” method with SMS TOTP.
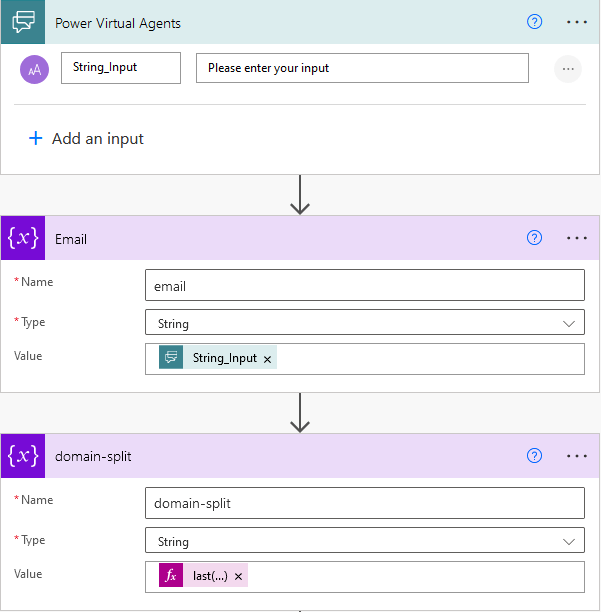
We will use the MFA custom policies from the starter pack.
The attribute used to provision SMS TOTP in the custom policy is “strongAuthenticationPhoneNumber”.
When the user signs in, you need to add these attributes to the Technical Policy (TP).
<OutputClaim
ClaimTypeReferenceId="Verified.strongAuthenticationPhoneNumber" />
The verified phone number is apparently for when the phone number is verified using the MFA flow.
And when you read the user attributes in a TP, you need to add:
Note that you need to redefine these in the schema by adding a “TextBox” element:
Verified phone Number
string
XXX-XXX-
Your office phone number that has been verified
TextBox
Verified phone Number
string
XXX-XXX-
Your office phone number that has been verified
TextBox
otherwise you will get errors.
I wrote a .NET Core command-line program to provision the phone number.
As usual, this is in a gist.
The application registration is as per the “Manage B2C with Graph API” article .
You need to add this API permission:

In the code:
// Replace with your Azure AD B2C app registration details.
var clientId = "cd...05";
var tenantId = "65...16";
var clientSecret = "iK...wy";
There are two types of MFA phone numbers whose IDs are:
// Choose the type of phone number to update:
// For mobile phone: "3179e48a-750b-4051-897c-87b9720928f7"
// For business/office phone: "e37fc753-ff3b-4958-9484-eaa9425c82bc"
The commands are:
ManagePhoneNumber.exe
Usage: ManagePhoneNumber [list|new|update|delete] userObjectID [phoneNumber]
[B|M] where B=Business phone and M=Mobile phone
Let’s list a user’s MFA phone number:
ManagePhoneNumber.exe list 5c...fa 11 M
Current phone authentication methods:
No phone authentication methods with a phone number found for this user.
Note that “List” just needs a dummy phone number.
This user is not proofed up for MFA, so run the sign-in policy for that user.
As expected, we are asked to proof up:

Let’s ignore that and add the phone number programmatically, then list it to verify.
ManagePhoneNumber.exe new 5c...fa +641234 M
New phone authentication method added successfully.
ManagePhoneNumber.exe list 5c...fa 11 M
Current phone authentication methods:
Method Id/Type: 3179e48a-750b-4051-897c-87b9720928f7, Phone Number: +641234
Run the sign-in policy for that user.
As expected, we are asked to verify the phone number:

Similarly, we can “update” or “delete” the phone number.
All good!
Provisioning user MFA programatically in Azure AD B2C was originally published in The new control plane on Medium, where people are continuing the conversation by highlighting and responding to this story.