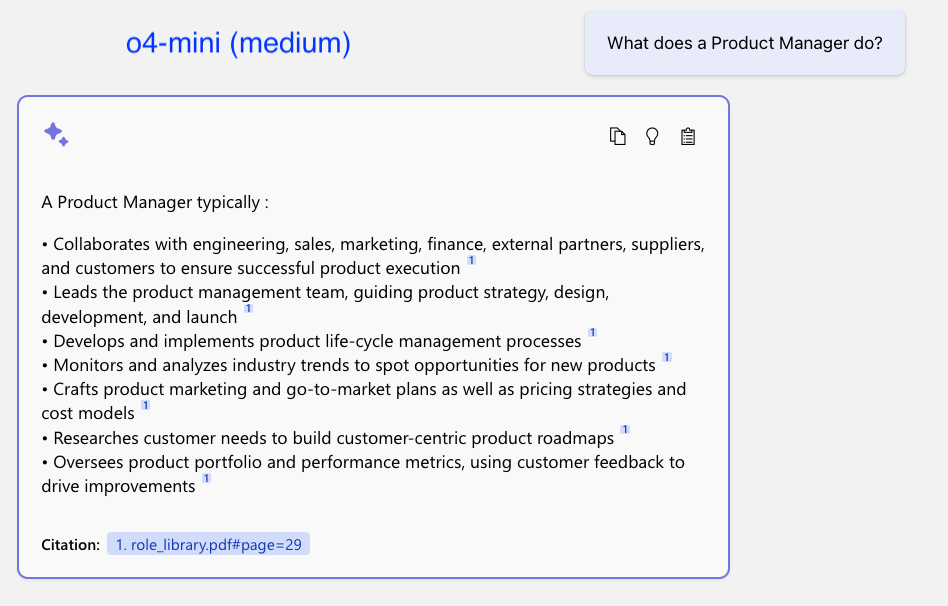
Finding the Right Page number in PDFs with AI Search
August 11, 2025New in Microsoft AppSource: July 23-31, 2025
August 12, 2025Summary
Microsoft recently disclosed CVE-2025-53770, a critical vulnerability affecting on-premises SharePoint Server versions 2016, 2019, 2010, 2013, and Subscription Edition (SE). The vulnerability allows unauthenticated remote code execution (RCE) by chaining two separate CVEs:
- CVE-2025-49706 – Authentication Bypass
- CVE-2025-49704 – Deserialization Vulnerability
Microsoft has released security updates for SharePoint Server 2016, 2019, and SE. Versions 2010 and 2013 are out of support and will not receive patches, leaving them exposed.
If exploited, this vulnerability could allow an attacker to bypass authentication, extract cryptographic keys, and execute arbitrary C# code on the server.
Technical details
On-premises SharePoint Servers are enterprise-grade collaboration platforms that organizations install and manage on their own infrastructure, typically in their data centers.
The attack chain for CVE-2025-53770 involves the following steps:
- CVE-2025-49706 – Authentication Bypass
The attacker sends a crafted POST request targeting the endpoint:/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx with a malicious Referer value:/_layouts/SignOut.aspxThis manipulates SharePoint into trusting the request and its payload. - CVE-2025-49704 – Deserialization Vulnerability
The attacker then sends a POST request with a serialized spinstall0.aspx payload, designed to extract MachineKey values from web.config.
These keys are then used to craft a serialized C# code payload embedded in a valid __VIEWSTATE, which SharePoint trusts and executes.
Microsoft guidance
We strongly recommend following Microsoft’s official mitigation steps outlined in the MSRC blog:
Customer guidance for SharePoint vulnerability CVE-2025-53770 | Microsoft Security Response Center
See the “How to protect your environment” section for patching guidance, configuration updates, and additional mitigation strategies.
Protecting with Azure Web Application Firewall
You can create a custom rule to help detect and block suspicious requests matching known indicators of this attack.
Example WAF custom rule:
- Condition 1: URI contains / _layouts/15/ToolPane.aspx or / _layouts/15/spinstall0.aspx
- Condition 2: Referer header contains / _layouts/SignOut.aspx or / _layouts/15/SignOut.aspx
JSON view
“customRules”: [ { “name”: “CVE202553770”, “priority”: 100, “ruleType”: “MatchRule”, “action”: “Block”, “matchConditions”: [ { “matchVariables”: [ { “variableName”: “RequestUri” } ], “operator”: “Regex”, “negationConditon”: false, “matchValues”: [ “(?i)/_layouts(?:/d+)?/(SignOut|spinstall0|ToolPane).aspx” ], “transforms”: [] }, { “matchVariables”: [ { “variableName”: “RequestHeaders”, “selector”: “Referer” } ], “operator”: “Regex”, “negationConditon”: false, “matchValues”: [ “(?i)/_layouts(?:/d+)?/(SignOut|spinstall0|ToolPane).aspx” ], “transforms”: [] } ], “skippedManagedRuleSets”: [], “state”: “Enabled” } ]
Next steps
- Patch immediately: Apply Microsoft’s updates for SharePoint 2016, 2019, and SE.
- Isolate legacy systems: SharePoint 2010 and 2013 remain vulnerable—consider restricting network access or migrating to supported versions.
- Deploy WAF protections: Add the custom rule above to monitor and block suspicious traffic targeting vulnerable endpoints.
You can find more information about Custom Rules on Azure WAF for Application Gateway here or for Azure Front Door here.
For more on Azure WAF, see:
Azure Web Application Firewall documentation