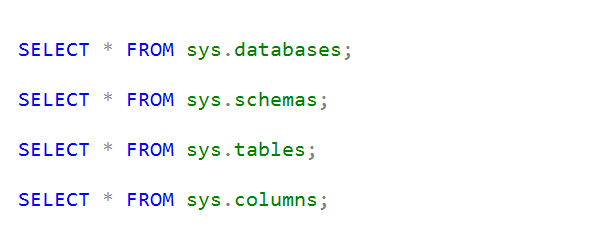
SDU Tools: List User-Defined Data Types in SQL Server
March 9, 2025
T-SQL 101: #127 Querying the SQL Server System Catalog
March 10, 2025
Entra External ID can currently be used as a SAML SP but not as an IDP.
The B2C SAML IDP configuration is described here.
As usual, the custom policy is in a gist.
Note that the key to B2C using SAML as the token issuer is:
<OrchestrationStep Order="8" Type="SendClaims"
CpimIssuerTechnicalProfileReferenceId="Saml2AssertionIssuer"/>
and in the RP, the protocol is:
The output claims from the RP are:
Note that email needs to be output as “emailaddress”.
In Entra External ID, under “All identity providers”, select “Custom”.
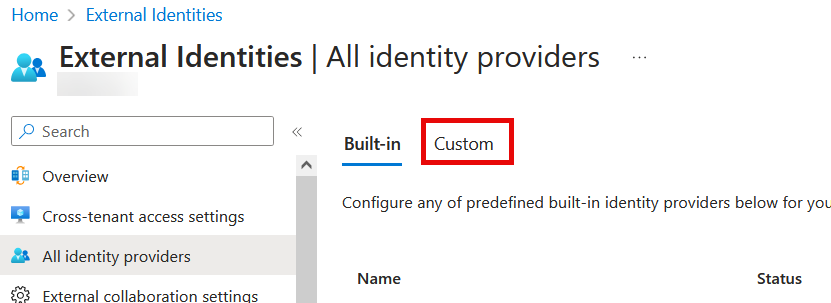
Then “Add new — SAML”:
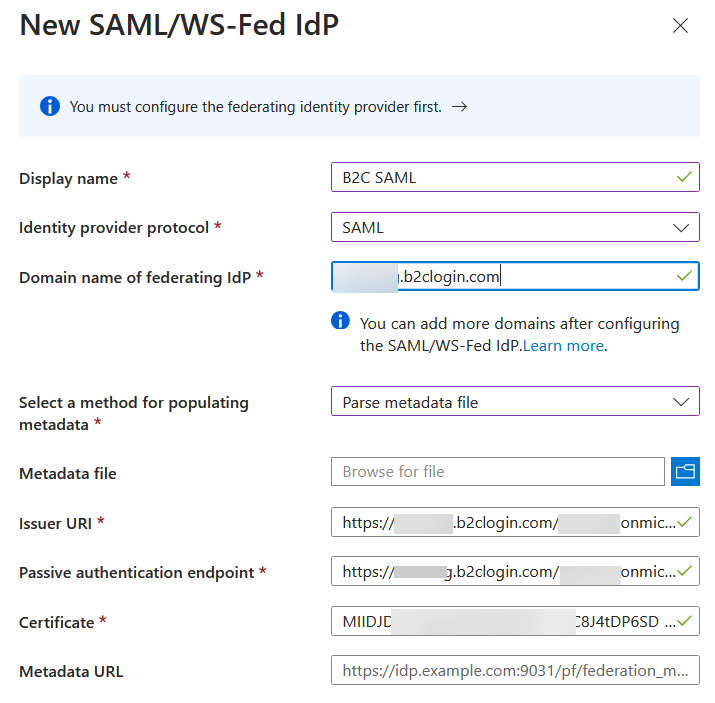
The domain name is:
tenant.b2clogin.com
I downloaded the B2C SAML metadata file from the URL:
https://tenant.b2clogin.com/tenant.onmicrosoft.com//
Samlp/metadata
and then imported it above.
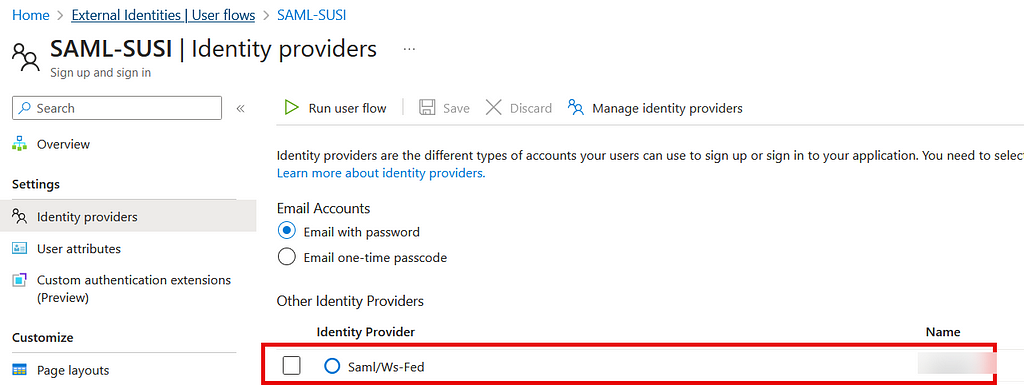
Add the new identity provider to the user flow:
Now, when you run the user flow from the portal, you see:
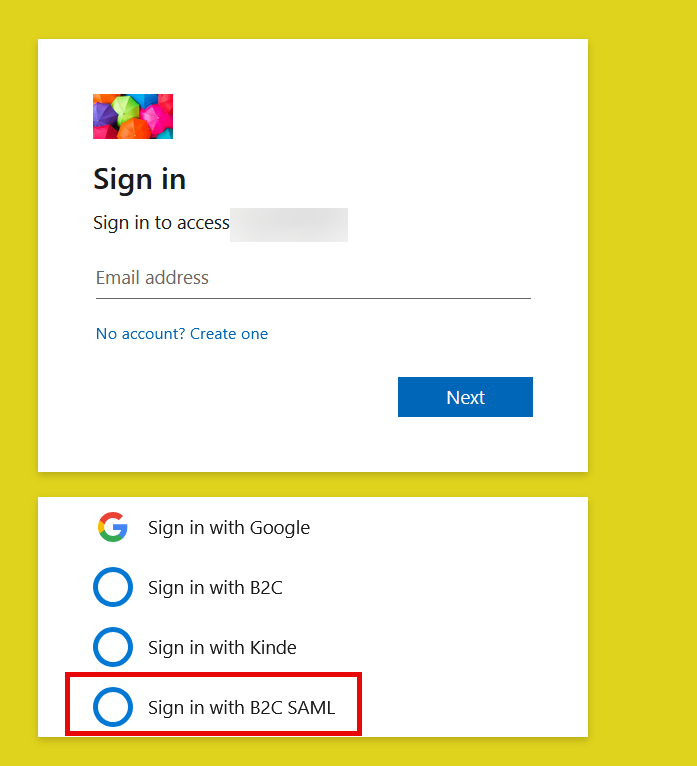
Click sign in with the B2C SAML provider.
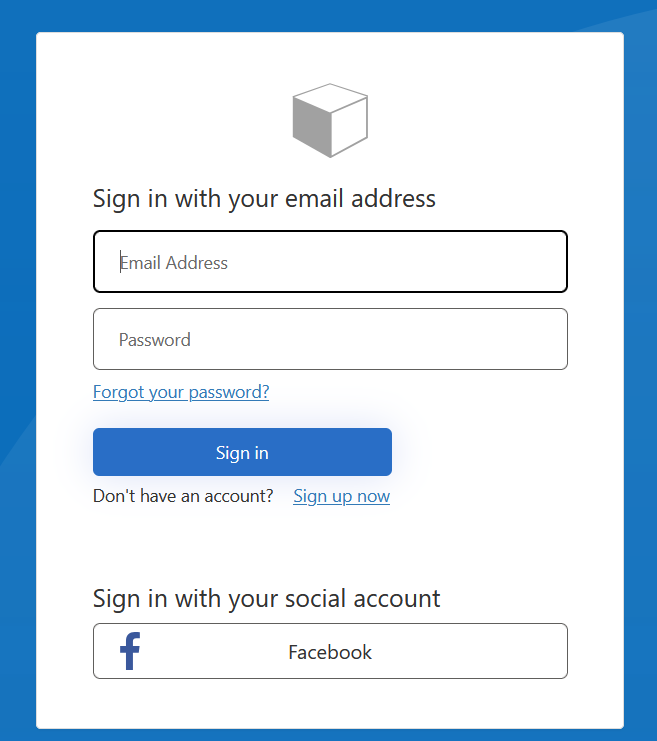
You should see the B2C login screen.
Sign in with your B2C user:
If this is the first user login, you are asked for extra details:
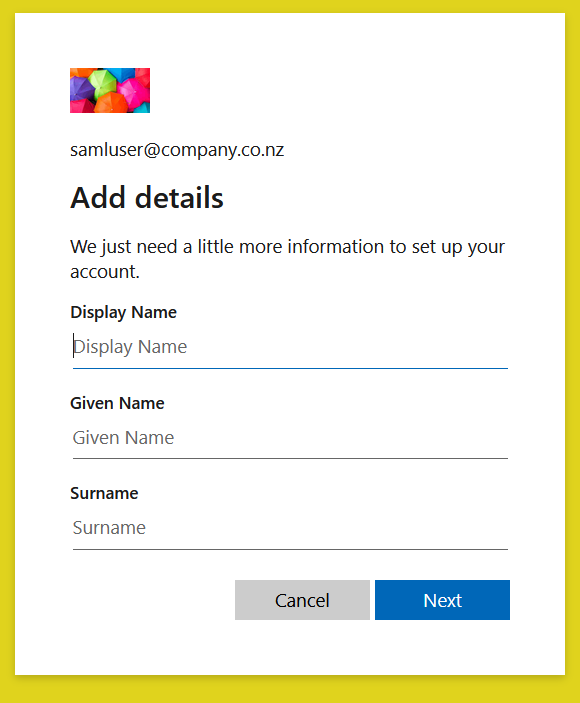
and the login is successful.
If you do a network trace after the sign in and look at the SAML packet:
<saml:Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims
/name"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"
FriendlyName="Display Name">
SAML User
<saml:Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims
/emailaddress"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"
FriendlyName="Email Address">
samluser@company.co.nz</saml:
AttributeValue>
<saml:Attribute Name="http://schemas.microsoft.com/identity/claims
/userprincipalname"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"
FriendlyName="UserPrincipalName">
841...e33@tenant.onmicrosoft.com
and the JWT returned is:
{
"aud": "302...3cc",
"iss": "https://7fb...3bb.ciamlogin.com/7fb...3bb/v2.0",
"iat": 1741482587,
"nbf": 1741482587,
"exp": 1741486487,
"aio": "AVQBq/4ZA...W7L",
"idp": "https://tenant.b2clogin.com/tenant.onmicrosoft.com/
B2C_1A_ExternalIDSigninSAML",
"nonce": "eao1QL_iMj",
"rh": "1.Abg...4AA.",
"sub": "t4p...L2k",
"tid": "7fb...3bb",
"uti": "MRm...BAA",
"ver": "2.0",
"Mail": "samluser@company.co.nz"
}
The External ID identity of the new user is:
and the user type is “Member”.
All good!
Connecting Entra External ID as an SP to Azure AD B2C via SAML was originally published in The new control plane on Medium, where people are continuing the conversation by highlighting and responding to this story.